It was all so easy: a story about privacy
06 Feb 2019
You are disappointed.
You have spent the last two months plotting an intricate location-tracking attack against your good friend, roommate, and mortal enemy, Steve Steveington. Your 9-step offensive would have combined metadata leaks, side-channel attacks and a sprinkle of social engineering, and would have given you realtime access to Steve’s smartphone’s exact location. Step 10 was going to be to use this information to trick him into buying more than his fair share of household groceries and to frame him for armed robbery.
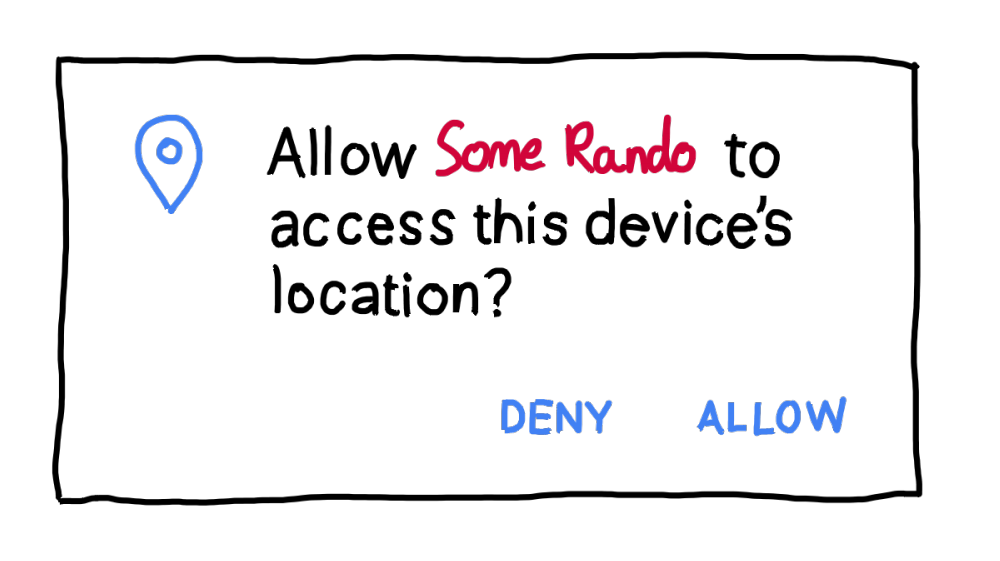
Step 1 started well. You got back in touch with your other good friend, Kate Kateberry, with whom you produced the Steve Steveington Show a few months ago. Kate recently started a new job at TinyLab, a company that makes low-quality children’s smartphone games that secretly track your location. When their games start up, they ask the user “Can we see your location at all times please?” If the user - who is either blind with desperation to play a bad clone of a successful children’s game, or else under the age of seven and therefore not really able to read or interpret long words - clicks “Yes”, then TinyLab can see the user’s location at all times and can helpfully funnel it back to their servers for later packaging and sale.
TinyLab is currently being sued by the state of New Mexico for child consumer privacy violations, so you add an “allegedly” to all of the above.
You strike a deal with Kate - if you can trick Steve into installing one of TinyLab’s games, she will give you access to the location data that it collects. You will pay her $5 for her troubles. With your inside woman in place, you are ready to initiate step 2 of your plan.
You pull the trigger one evening while you are kicking back with the Stevester, watching the Food Channel and eating some breakfast cereal for dinner. “Hey Steve,” you ask, innocently, “could we install Fun Kids Train 2: Dinosaur Park Race on your phone? It’s meant to be a creative work of rare, raw genius but only runs on Android.” You are certain that SS will see through this obvious ruse, but it is a necessary setup for steps 3, 4, 5 and 7 of your masterplan.
Incredibly, however, Steve grunts in the affirmative. Without taking his eyes off the TV or his spoon out of his mouth, he downloads Fun Kids Train 2: Dinosaur Park Race. He signs up for an account using his email address, and tosses you his phone. Caught completely off-guard, you suppose that you had better start playing. It takes you 3 minutes to decide that, despite its name, Fun Kids Train 2: Dinosaur Park Race is not a very fun game, but you keep playing for another 4 hours so as not to arouse suspicion. When you finally finish you drag Fun Kids Train 2: Dinosaur Park Race into the Stevemeister’s “Games” folder and leave it to quietly hoover up his location data.
The next morning you call up Kate Kateberry. Yuh huh, she says, I see Steve’s account. Let me make a live feed of his location data for you. You hang up and sadly cross out steps 3 through 9 of your magnum opus. You pull down Steve’s location data from Kate’s feed. You successfully use the data to trick him into buying more than his fair share of household groceries and to frame him for armed robbery. After 9 months and $25,000 of protracted legal battles he gets off scot-free, so no harm, no foul. You should feel happy, you tell yourself. But you just feel disappointed.
It was all so easy.
You are disappointed.
You have spent the last two months plotting an intricate location-tracking attack against your good friend, roommate, and mortal enemy, Steve Steveington. Your 9-step offensive would have combined metadata leaks, side-channel attacks and a sprinkle of social engineering, and would have given you realtime access to Steve’s smartphone’s exact location. Step 10 was going to be to use this information to trick him into buying more than his fair share of household groceries and to frame him for armed robbery.

Step 1 started well. You got back in touch with your other good friend, Kate Kateberry, with whom you produced the Steve Steveington Show a few months ago. Kate recently started a new job at TinyLab, a company that makes low-quality children’s smartphone games that secretly track your location. When their games start up, they ask the user “Can we see your location at all times please?” If the user - who is either blind with desperation to play a bad clone of a successful children’s game, or else under the age of seven and therefore not really able to read or interpret long words - clicks “Yes”, then TinyLab can see the user’s location at all times and can helpfully funnel it back to their servers for later packaging and sale.
TinyLab is currently being sued by the state of New Mexico for child consumer privacy violations, so you add an “allegedly” to all of the above.
You strike a deal with Kate - if you can trick Steve into installing one of TinyLab’s games, she will give you access to the location data that it collects. You will pay her $5 for her troubles. With your inside woman in place, you are ready to initiate step 2 of your plan.
You pull the trigger one evening while you are kicking back with the Stevester, watching the Food Channel and eating some breakfast cereal for dinner. “Hey Steve,” you ask, innocently, “could we install Fun Kids Train 2: Dinosaur Park Race on your phone? It’s meant to be a creative work of rare, raw genius but only runs on Android.” You are certain that SS will see through this obvious ruse, but it is a necessary setup for steps 3, 4, 5 and 7 of your masterplan.
Incredibly, however, Steve grunts in the affirmative. Without taking his eyes off the TV or his spoon out of his mouth, he downloads Fun Kids Train 2: Dinosaur Park Race. He signs up for an account using his email address, and tosses you his phone. Caught completely off-guard, you suppose that you had better start playing. It takes you 3 minutes to decide that, despite its name, Fun Kids Train 2: Dinosaur Park Race is not a very fun game, but you keep playing for another 4 hours so as not to arouse suspicion. When you finally finish you drag Fun Kids Train 2: Dinosaur Park Race into the Stevemeister’s “Games” folder and leave it to quietly hoover up his location data.
The next morning you call up Kate Kateberry. Yuh huh, she says, I see Steve’s account. Let me make a live feed of his location data for you. You hang up and sadly cross out steps 3 through 9 of your magnum opus. You pull down Steve’s location data from Kate’s feed. You successfully use the data to trick him into buying more than his fair share of household groceries and to frame him for armed robbery. After 9 months and $25,000 of protracted legal battles he gets off scot-free, so no harm, no foul. You should feel happy, you tell yourself. But you just feel disappointed.
It was all so easy.